TIM Professional offers two methods of securing your system:
- console based - to protect the actual application
- network based - to allow only particular information to reach certain clients
Both methods require the main administrator to set up the users and passwords using the entry screen.
Access the top-left menu and select View -> Users and passwords. In the new window that appears click on the button to add a new user. The following window will pop up
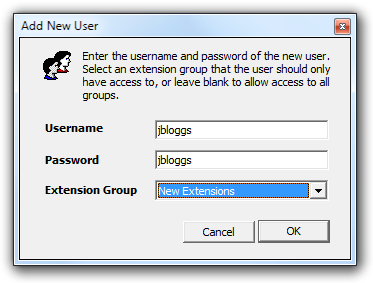
Within this screen, you can configure each of the two methods of protection, by following the procedure below:
Console Locking
Set up a user with the username console (all characters in lower case), enter a password, then select (Console Access) from the Extension Group drop-down list. Click on the button to add the console user to the list.
Only one user named console can be setup for Console Access. |
Briefly, there are two methods of protection: console based (to protect the actual application) and network-based (to allow only particular information to reach certain clients).
Both methods require the main administrator to setup users and passwords using a simply entry screen.
The following screen is accessible from the View ? Users & passwords... menu.
Add a user by clicking the  button, then entering the details into the new window that appears...
button, then entering the details into the new window that appears...

Once you click the  button, the following window pops up:
button, the following window pops up:

Using this simple entry screen, you can set each of the two methods of protection by following the procedures here:
Console Locking
Set up a user with a username console (in lower case), choose a password, then select (Console Access) from the Extension Group drop-down list. Click on the button, and the user will appear in the list. Only one user (named console) can be setup for Console Access.
Web Username restrictions
When running reports, the extension groups that are accessible can be forcibly restricted to a single group. This is most often used in an organisation where a department manager is given access only to his/her own information, and no-one else's.
Additionally, any number of users may be setup who may access all extension groups' data.
To setup a user who may only view a single group of extensions, simply click on the  button on the Users & passwords... screen (as described above). In the Add New User window that appears, enter a username and a password of your choice, but from the Extension Group drop-down list, choose the extension group to whom this user is granted access.
button on the Users & passwords... screen (as described above). In the Add New User window that appears, enter a username and a password of your choice, but from the Extension Group drop-down list, choose the extension group to whom this user is granted access.
To add a user who may access all extensions, leave the Extension Group drop-down list empty (the default), or select the blank item at the top of the list.
A user who has access to all extension information will be shown in the
User List with a ![]() icon, as opposed to a
restricted user, a
icon, as opposed to a
restricted user, a ![]() symbol.
symbol.